Cybersecurity or information technology security (IT security) is the protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
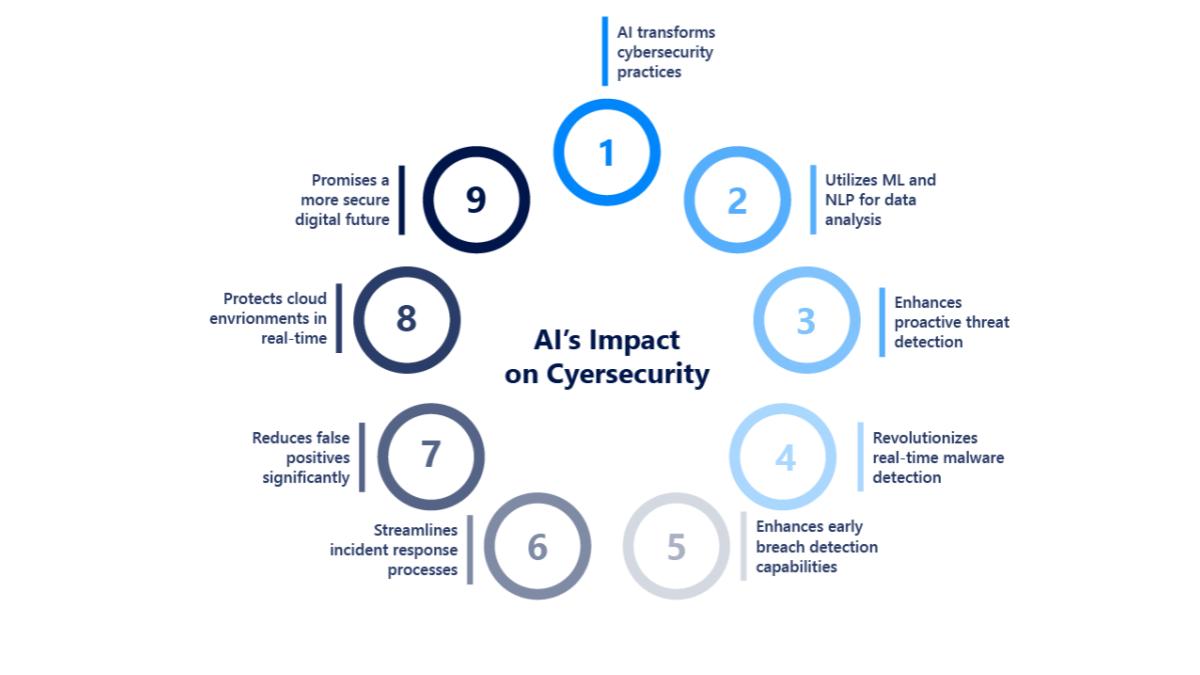
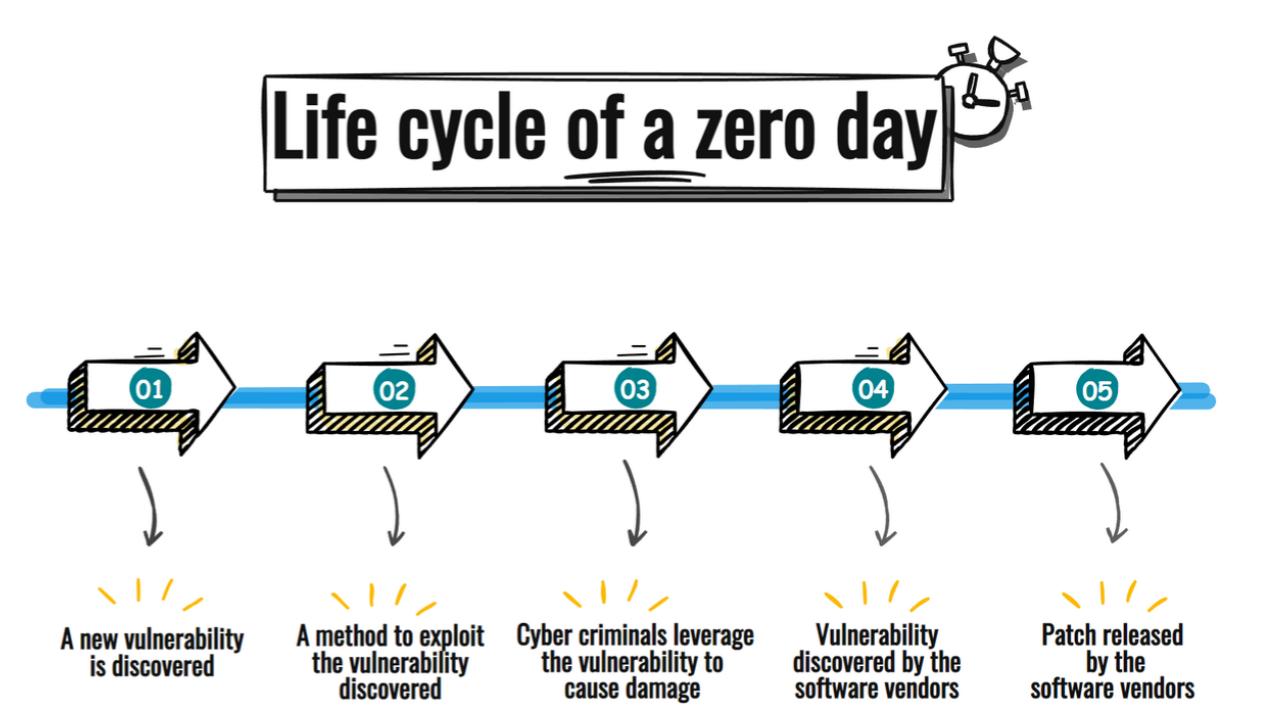
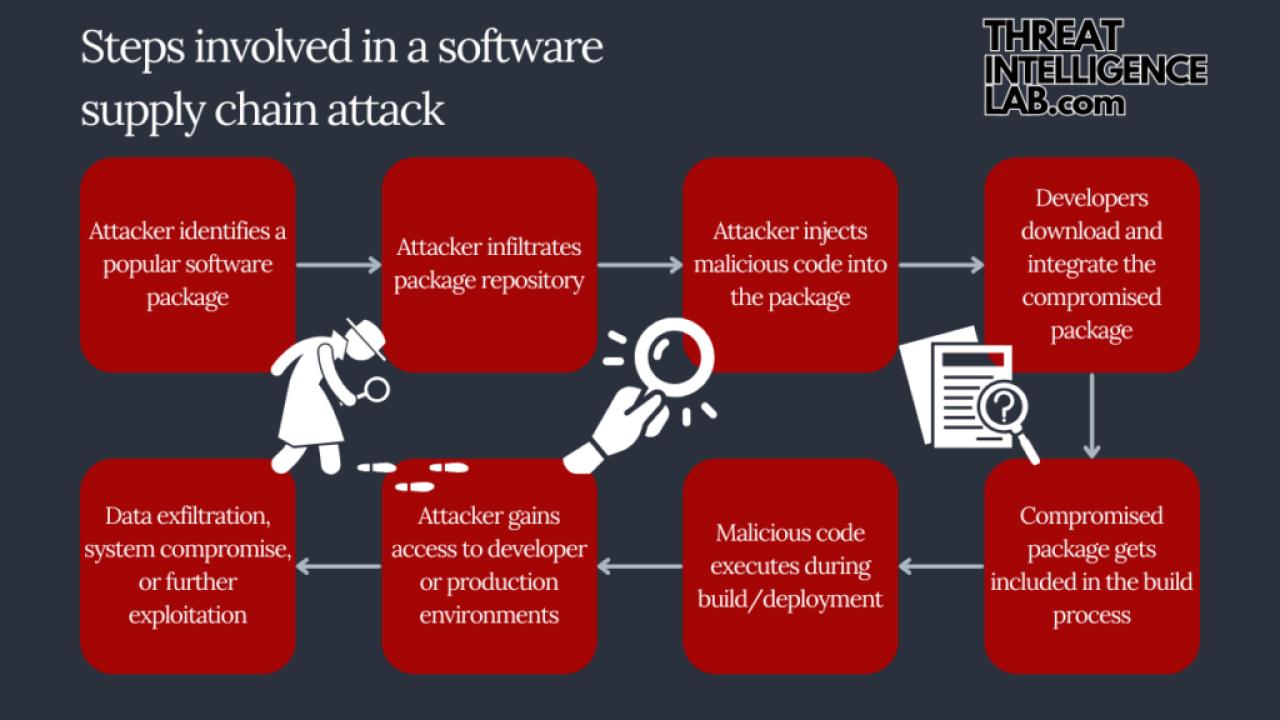
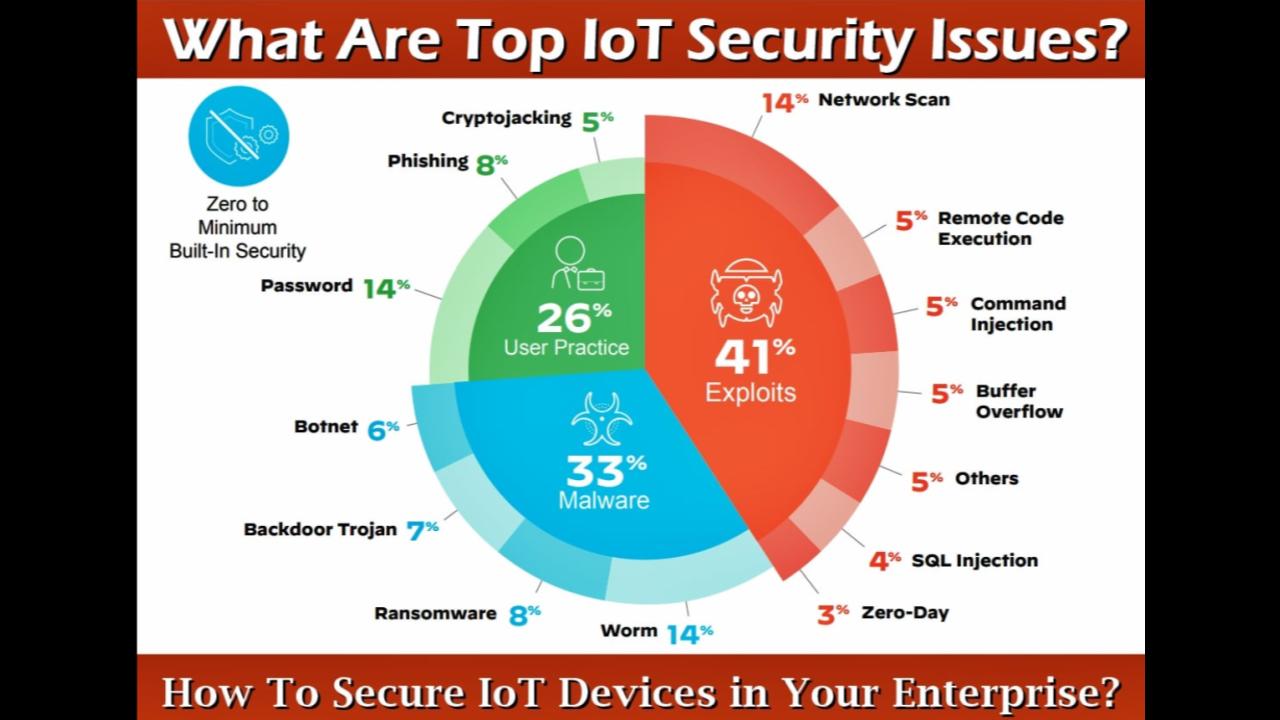
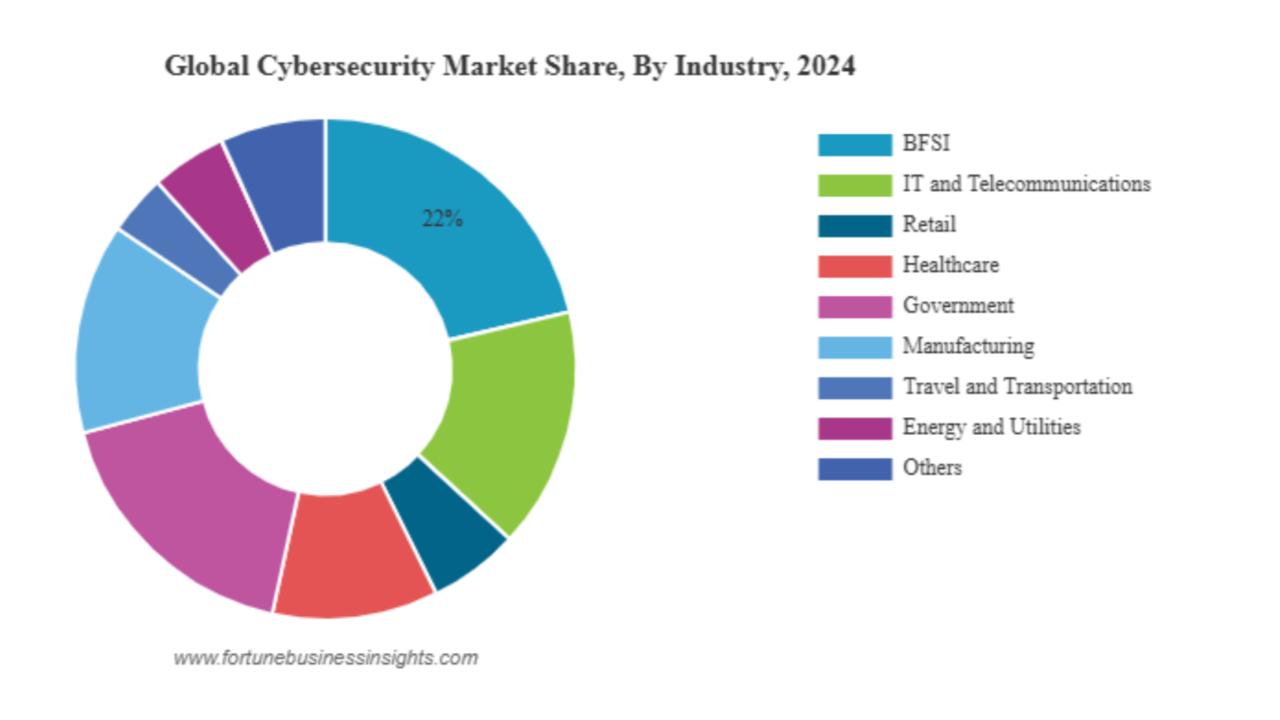
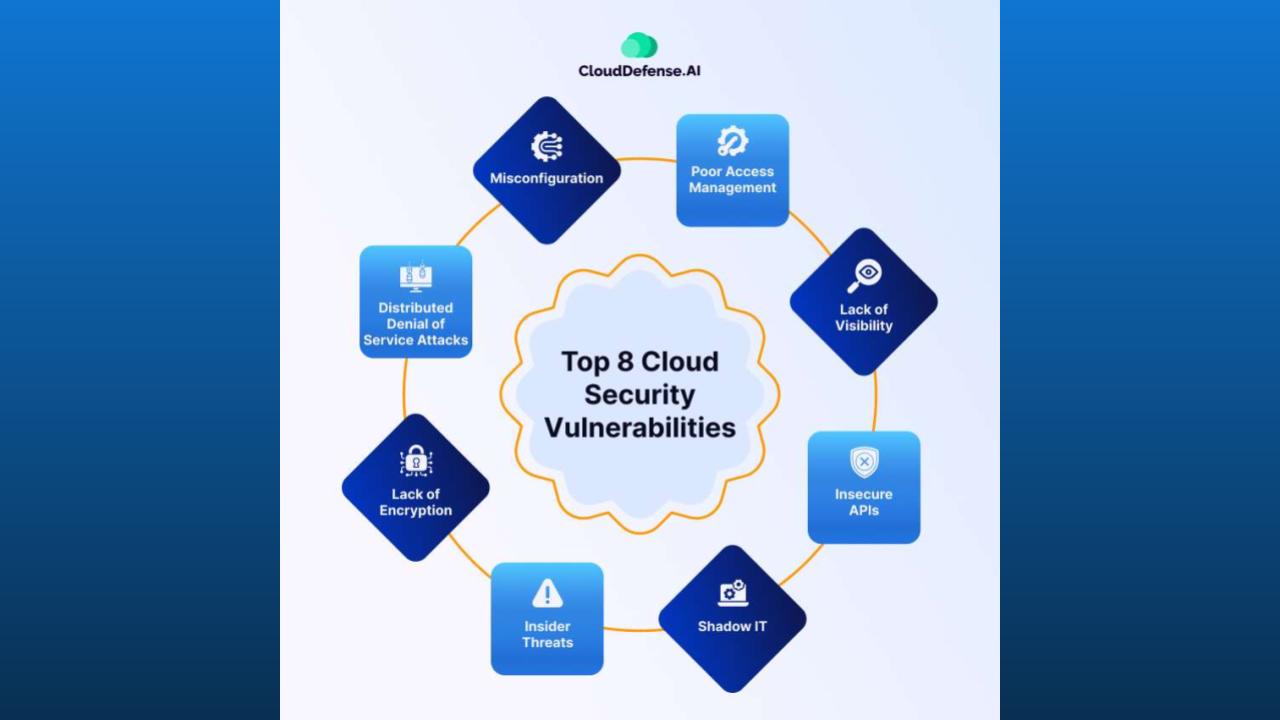
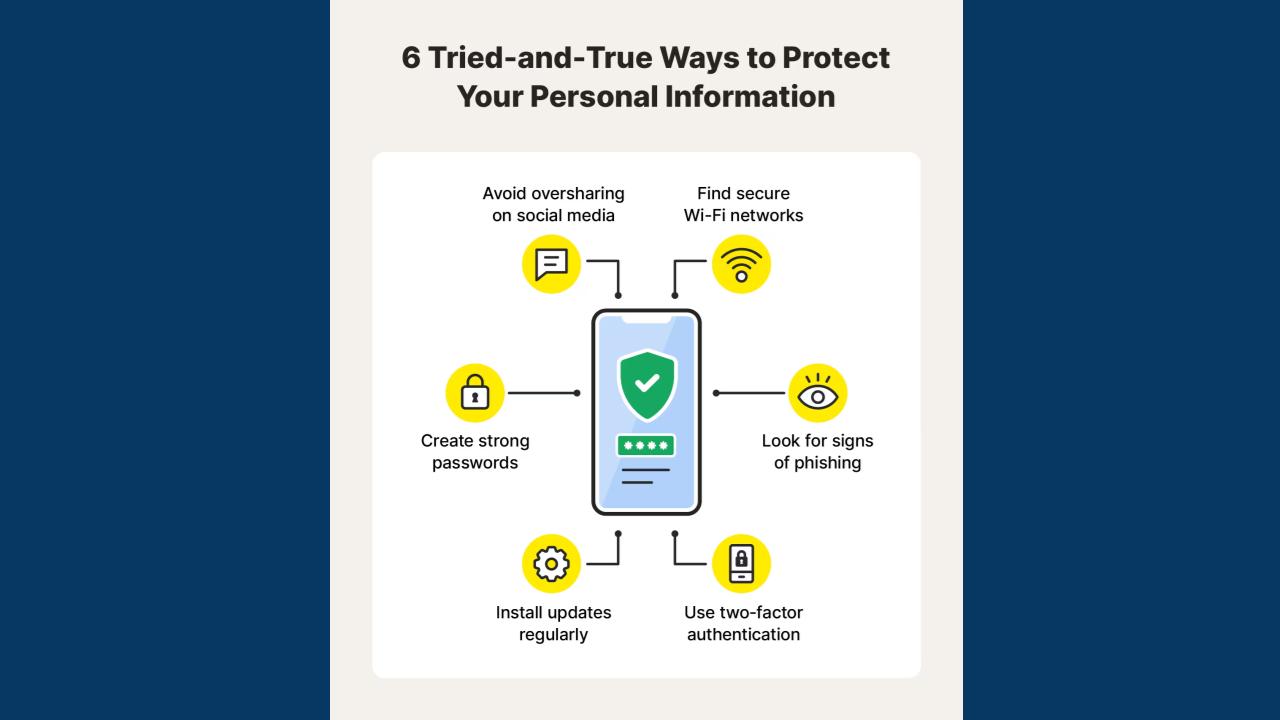
Top cybersecurity challenges include evolving ransomware, AI-powered attacks, advanced social engineering, and securing multi-cloud environments. The increasing use of AI by both attackers and defenders is rapidly shaping the threat landscape, while the expansion of remote work has broadened the attack surface for vulnerabilities in areas like IoT devices and supply chains.
OnAir Post: Cyber Challenges