Summary
A zero-day vulnerability is a software or hardware security flaw that is unknown to the vendor or the public.
The term “zero-day” refers to the fact that the developers have had “zero days” to discover or fix the flaw before it is exploited by malicious actors in a zero-day attack.
OnAir Post: Zero-day Vulnerabilities
About
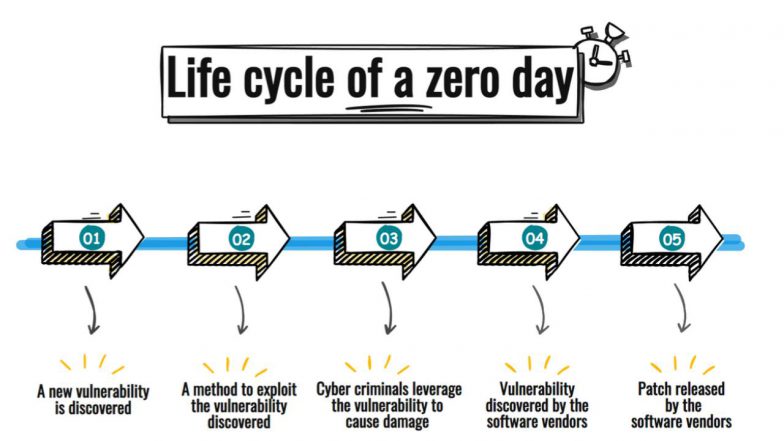
How They Work
- Discovery: An attacker or security researcher uncovers a flaw in the code or design of a software, hardware, or firmware product.
- Weaponization: The attacker develops an exploit, which is a specific method or piece of code designed to take advantage of that particular vulnerability.
- Deployment: The exploit is delivered to target systems, often through phishing emails, malicious websites (drive-by downloads), or direct network attacks.
- Exploitation: The exploit runs on the vulnerable system, allowing the attacker to steal data, install more malware (like ransomware or spyware), gain unauthorized access, or disrupt operations.
- Detection and Patching: Eventually, the unusual activity is detected, the vulnerability is publicly disclosed, and the vendor races to develop and release a patch. The window between initial exploitation and patch deployment is when the vulnerability poses the greatest risk.
Source: Gemini AI Overview – 11/6/2025
Risks and Impacts
Zero-day vulnerabilities are dangerous because they are often undetected by traditional security tools that rely on known threat signatures. This can result in data breaches, operational disruptions in critical infrastructure and government operations, and significant financial and reputational damage to organizations. Attackers can also use them to remain hidden in compromised systems for long periods.
Real-World Examples
Notable zero-day exploits include Stuxnet (2010), which damaged Iran’s nuclear program by exploiting Windows vulnerabilities, the Microsoft Exchange Server hacks in 2021 that were used for cyber espionage, and the critical Log4Shell vulnerability (2021) in the Log4j library that affected millions of devices
Protection and Mitigation
- Applying vendor patches promptly for known vulnerabilities reduces the overall attack surface.
- Using advanced security tools that analyze behavior rather than just relying on signatures can help detect novel attacks.
- Implementing a zero-trust security model limits an attacker’s movement within a network.
- Network segmentation can help contain an attack’s impact.
- Educating users about phishing and other social engineering tactics, which are often used to deliver zero-day exploits, is also crucial.