Summary
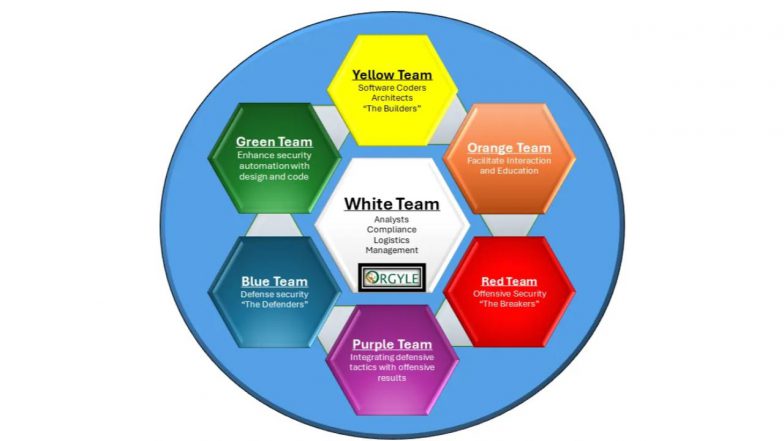
The cybersecurity white team acts as the oversight and management authority for security exercises (such as red team vs. blue team drills), ensuring the activity is controlled, safe, legal, and educational. They are neutral observers who do not participate in offensive or defensive actions directly.
OnAir Post: White Team
About
Source: Gemini AI Overview – 11/6/2025
Key functions of a cybersecurity white team include:
- Exercise Planning and Scenario Design: Designing the objectives and scope of security exercises, creating realistic scenarios, and establishing clear rules of engagement and timelines for all participating teams.
- Coordination and Communication: Orchestrating the activities of the red and blue teams, facilitating communication between different groups, and making real-time decisions about the exercise’s progression.
- Rule Enforcement and Adjudication: Acting as “referees” to ensure all participants follow the established rules, mediating disputes between teams, and ensuring fair play.
- Safety and Risk Management: Ensuring that the simulated attacks remain within a controlled environment and do not cause unintended damage to live production systems or operations.
- Monitoring and Data Collection: Observing and tracking the actions and performance of both the red and blue teams, and collecting data on all activities and findings for later analysis.
- Post-Exercise Analysis and Reporting: Compiling comprehensive reports after the exercise that document what worked well, what vulnerabilities were identified, and what areas need improvement.
- Providing Feedback and Training: Offering objective feedback to all teams to help them improve their skills, and coordinating regular training sessions to enhance the organization’s overall security posture.
- Compliance and Policy Enforcement: Ensuring that all security activities, exercises, and resulting remediation efforts align with the organization’s security policies, industry standards, and regulatory requirements.
- Incident Response Coordination (in a real incident context): In some operational structures, the white team may also coordinate the overall incident response effort during a real breach to ensure actions are well-orchestrated and effective.