Summary
A supply chain cyber attack is a type of cyberattack where a threat actor infiltrates an organization’s systems by compromising a less-secure or vulnerable element within its external network of suppliers, vendors, or software/hardware providers.
Attackers exploit the inherent trust between organizations and their partners, leveraging a single point of entry to gain access to numerous downstream targets simultaneously.
OnAir Post: Supply Chain Attacks
About
How They Work
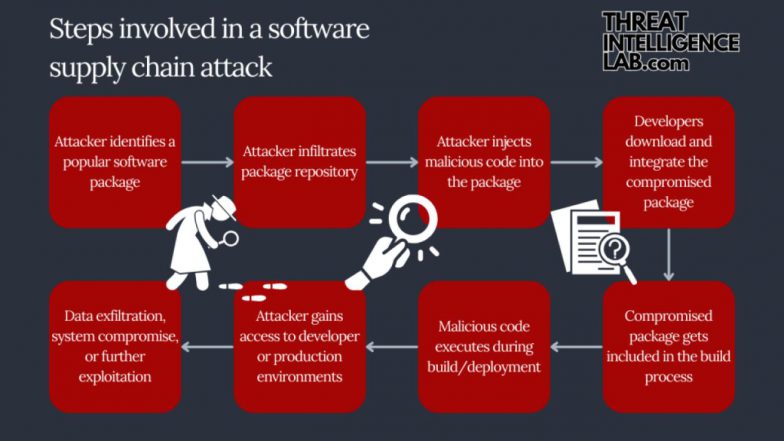
- Reconnaissance: Attackers identify third-party vendors or components (software, hardware, or services) used by the target organization, focusing on those with weaker security.
- Compromise: The attacker breaches the supplier’s system, often using methods like phishing to steal credentials, exploiting software vulnerabilities (zero-days), or physically tampering with products during manufacturing.
- Malicious Injection: Once inside the supplier’s environment, the attacker introduces malicious code into legitimate products, software updates, or open-source libraries that the supplier distributes to its customers.
- Infiltration: The target organization unknowingly installs the compromised update or uses the infected product. Because it comes from a trusted source and often has a valid digital signature, it typically bypasses traditional security defenses.
- Execution and Escalation: The malware activates within the target’s network, granting the attacker access to sensitive data, allowing for lateral movement, privilege escalation, and execution of their objective, whether it’s data exfiltration, deploying ransomware, or conducting espionage.
Source: Gemini AI Overview – 11/6/2025
Major Examples
- SolarWinds (2020): One of the most significant supply chain attacks in history, where Russian state-sponsored hackers injected a backdoor (SUNBURST) into the company’s Orion network management software updates. This led to the compromise of thousands of organizations, including multiple U.S. government agencies and Fortune 500 companies.
- MOVEit Transfer (2023): Attackers exploited a critical vulnerability in the MOVEit file transfer software to steal sensitive data from hundreds of organizations globally, including British Airways and the BBC, resulting in massive data breaches and financial losses.
- NotPetya (2017): Initially appearing as ransomware, this malware attack spread globally through a compromised update mechanism of M.E.Doc, a widely used Ukrainian accounting software. It caused billions of dollars in damage and severely disrupted critical infrastructure and global commerce.
- Target Data Breach (2013): Cybercriminals accessed Target’s systems by stealing credentials from a third-party HVAC vendor through a phishing email. This allowed them to access the payment card information of over 40 million customers.
- 3CX (2023): The desktop application for this widely used voice and video chat software was compromised, distributing malware to users via trojanized software installers signed with valid certificates.
Impact and Prevention
- Rigorous Vendor Management: Conducting thorough security assessments and continuous monitoring of third-party vendors and suppliers.
- Zero Trust Architecture (ZTA): Implementing a zero-trust model that requires continuous verification of every user and device, even within the network perimeter.
- Employee Training: Educating staff to identify and report phishing attempts and social engineering tactics.
- Software Integrity Controls: Using code-signing, hashing, and software composition analysis (SCA) tools to verify the integrity of all software components and updates.
- Incident Response Planning: Developing and rehearsing a specific incident response plan for a potential vendor compromise.