Summary
These challenges can lead to serious consequences, including large-scale botnet attacks (like the Mirai botnet), data breaches, and the disruption of critical physical systems such as medical devices or industrial controls.
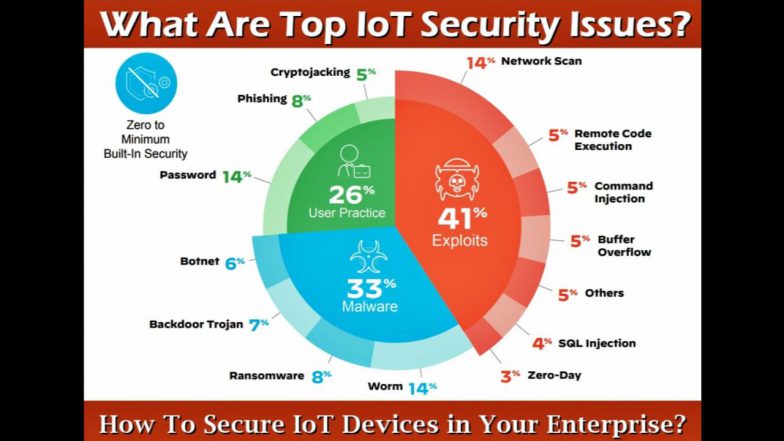
The primary cybersecurity challenges with Internet of Things (IoT) devices stem from their design priorities (convenience and low cost over security), limited processing power, and complex, unstandardized ecosystems
OnAir Post: Internet of Things Threats
About
Key challenges
- Weak/Default Authentication: Many devices ship with easily guessable or hardcoded default passwords that users often fail to change, providing an easy entry point for attackers.
- Lack of Regular Updates and Patching: Many IoT devices are not designed to receive regular security updates or firmware patches. This leaves vulnerabilities exposed long after they are discovered, and the manual intervention often required for updates is not always feasible across large deployments.
- Limited Computational Power: To keep costs and power consumption low, many devices have limited processing capacity, which prevents them from running robust security software like firewalls, full encryption, or antivirus programs.
- Insecure Data Transfer and Storage: A significant amount of data collected by IoT devices is transmitted over networks without proper encryption, making it vulnerable to interception (man-in-the-middle attacks) and manipulation.
- Lack of Standardization: There is no universal, industry-wide set of security standards, leading to a fragmented ecosystem with inconsistent security protocols and guidelines across different manufacturers and device types.
- Increased Attack Surface: The sheer volume and diversity of connected devices (billions globally) mean a vast number of potential entry points into a network. A single insecure device can be a gateway to an entire corporate or home network.
- Physical Security Weaknesses: IoT devices are often deployed in public or remote, unmanaged locations, making them susceptible to physical tampering, theft of components (like SIM cards), or unauthorized access to hardware.
- Data Privacy Concerns: Devices collect vast amounts of sensitive personal and operational data, often without transparent policies on how that data is used or stored, raising significant privacy risks.
- Lack of Device Visibility and Management: Organizations often struggle to maintain a full inventory of all connected IoT devices on their networks, making it difficult to monitor for suspicious activity, enforce security policies, or respond to incidents effectively.