Summary
The best way to understand cloud vulnerabilities is to combine continuous monitoring with a multi-layered testing approach and contextual analysis of risk. You should start by using automated tools like vulnerability scanners and Cloud Security Posture Management (CSPM) to identify known issues, then perform penetration testing to find weaknesses.
Crucially, analyze vulnerabilities based on business context and threat actor motives to prioritize those with the highest potential impact.
Source: Gemini AI Overview – 11/6/2025
OnAir Post: Cloud Vulnerabilities
About
Source: Gemini AI Overview – 11/6/2025
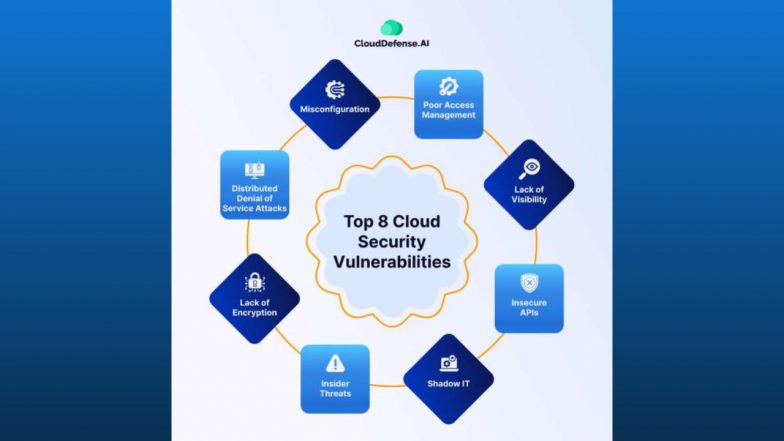
The top 10 cloud vulnerabilities for 2025 are primarily rooted in misconfiguration and identity issues, according to reports from security experts like the Cloud Security Alliance (CSA) and OWASP.
- Cloud Misconfigurations: This is consistently cited as the most common and critical vulnerability. Errors in setting up cloud resources (e.g., publicly exposed storage buckets, misconfigured security groups, or leaving default passwords in place) create easy entry points for attackers.
- Inadequate Identity and Access Management (IAM): Weaknesses in access controls, such as overly permissive permissions, lack of Multi-Factor Authentication (MFA), and failure to implement the principle of least privilege, allow attackers to compromise accounts and move laterally within an environment.
- Insecure APIs: APIs are fundamental to cloud services, but poor design, weak authentication, or a lack of input validation can expose sensitive data and systems.
- Account Hijacking/Credential Theft: Cybercriminals use methods like phishing and credential stuffing to steal legitimate credentials, allowing them to gain unauthorized access to cloud accounts and sensitive data.
- Lack of Visibility and Monitoring: The dynamic nature and complexity of cloud environments make it difficult to gain a comprehensive view of all resources and activities. Inadequate logging and monitoring hinder timely detection and response to security incidents.
- Insider Threats: Both malicious and accidental actions by employees, contractors, or third-party vendors with legitimate access can lead to data breaches or system compromise.
- Data Breaches and Loss: The exposure or loss of sensitive data remains a top risk, often resulting from other vulnerabilities like misconfigurations or weak access controls.
- Vulnerable and Outdated Components: Using unpatched or unsupported software, libraries, and frameworks can expose applications to known security flaws, which attackers actively exploit.
- Denial of Service (DoS) Attacks: These attacks aim to disrupt the availability of cloud services by overwhelming them with traffic, causing downtime and significant operational impact.
- Shadow IT: The use of unauthorized cloud services or applications by employees creates security blind spots, as these services often lack proper security controls and oversight from IT teams.
How best to address
Source: Other
Ongoing security and detection
- Continuous monitoring: Implement solutions that provide constant visibility into your cloud environment to detect unusual activities and new vulnerabilities as they emerge.
- Automated vulnerability scanning: Set up regular, automated scans to continuously identify new vulnerabilities in all assets, including new deployments.
- Regular penetration testing: Conduct penetration tests to identify weaknesses and validate the effectiveness of your security controls.
- Security assessments: Perform regular security assessments to evaluate your policies, practices, and tools, ensuring they align with current threats and compliance standards.
Access and identity management
- Implement a Zero Trust architecture: Adopt a “never trust, always verify” approach to limit access to resources and minimize the potential damage from a single breach.
- Use strong IAM controls: Implement robust Identity and Access Management by enforcing the principle of least privilege, using role-based access control (RBAC), and requiring strong, ideally passwordless, multi-factor authentication (MFA) for all users.
- Manage misconfigurations: Focus on misconfigurations, which are a leading cause of breaches. Audit access controls regularly and train employees to prevent them.
Remediation and development
- Prioritize based on risk: Prioritize remediation based on business impact, not just vulnerability scores. Assess exploitability and other contextual factors to determine the urgency of a fix.
- Automate remediation: Use automation to apply patches and fixes quickly, especially for high-risk issues.
- Integrate security into development: Shift security left by embedding vulnerability scanning and other security checks directly into your CI/CD pipeline to catch issues before they reach production.
- Patch management: Keep all software and systems updated with the latest security patches, using virtual patching as a temporary solution if necessary.
Tools and training
- Leverage security tools: Use specialized cloud security tools like Cloud Security Posture Management (CSPM), Cloud Workload Protection Platforms (CWPP), and Cloud Access Security Brokers (CASB) to gain visibility and automate security.
- Encrypt data: Encrypt sensitive data both at rest and in transit using strong encryption methods.
- Train your staff: Regularly train your team on secure cloud practices, social engineering defense, and your organization’s specific security standards to reduce human error.
Planning and response
- Create a backup and disaster recovery plan: Have a strategy in place to recover from incidents or vendor outages.
- Establish an incident response plan: Have a clear plan in place for how to respond to a security incident.