Summary
A cybersecurity purple team’s primary function is to integrate the offensive strategies of red teams with the defensive strategies of blue teams to ensure continuous feedback, identify security gaps, and improve an organization’s overall security posture.
It functions as a collaborative bridge, not necessarily a separate, permanent team, that maximizes the efforts of both sides.
OnAir Post: Purple Team
About
Source: Gemini AI Overview – 11/6/2025
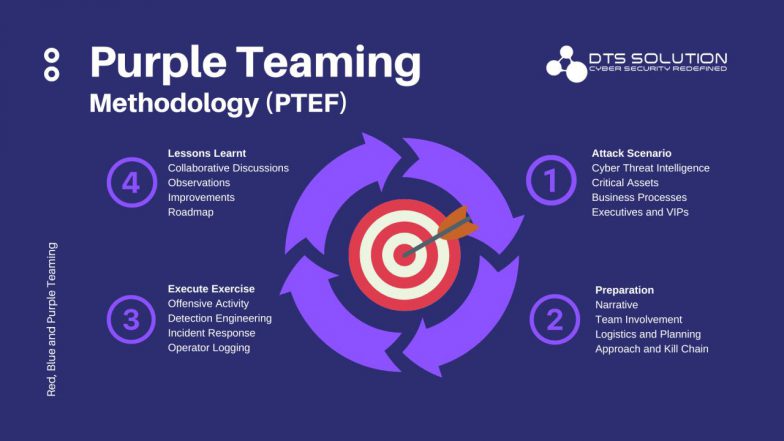
Key functions of a purple team include:
- Facilitating Collaboration and Communication: The purple team ensures effective, real-time communication between red and blue teams, breaking down traditional operational silos and fostering a shared goal of enhanced security.
- Coordinating Exercises: They design, scope, and coordinate joint attack simulations and defensive exercises, often using frameworks like the MITRE ATT&CK, to ensure they are aligned with the organization’s specific risks and objectives.
- Translating Insights into Actionable Defense: A crucial function is converting the red team’s offensive findings (e.g., successful attack paths, exploited vulnerabilities, and TTPs) into concrete, actionable defensive measures for the blue team, such as new detection rules or refined incident response playbooks.
- Improving Detection and Response Capabilities: By observing how effectively the blue team detects and responds to simulated attacks, the purple team helps fine-tune security tools (like SIEM and EDR systems) and response protocols, ultimately reducing the time it takes to detect and mitigate real threats.
- Training and Skill Development: Purple team exercises provide valuable, hands-on training opportunities for both offensive and defensive personnel, cross-training them on both attack methodologies and defensive strategies.
- Documenting and Reporting Findings: They ensure all activities, findings, vulnerabilities, and recommendations are thoroughly documented. This results in comprehensive reports that help track progress and demonstrate proactive security management to stakeholders and compliance authorities.
- Ensuring Continuous Improvement: The purple team approach emphasizes an iterative feedback loop. Findings from one exercise inform improvements that are then re-tested in subsequent simulations, leading to a more mature and resilient security posture over time.
- Validating Security Controls: They help validate the effectiveness of existing security investments and controls, ensuring that tools and procedures are working as intended in a real-world context.