Summary
Backdoors & Breaches is a tabletop card game that simulates a cyber attack, designed to train and improve the incident response skills of cybersecurity teams.
Inspired by role-playing games like Dungeons & Dragons, it offers a fun and conversational approach to a tabletop exercise.
Yes, there are multiple open-source and free online versions of the Backdoors & Breaches card game. While the original physical card deck is sold by Black Hills Information Security, the company supports and promotes the use of open-source projects for playing the game remotely
Black Hills Information Security – 31/03/2022 (59:03)
Chapters
0:00 intro to team and Backdoors & Breaches story
2:23 Online open source game copy
3:15 Why we sell physical copies and info for educators
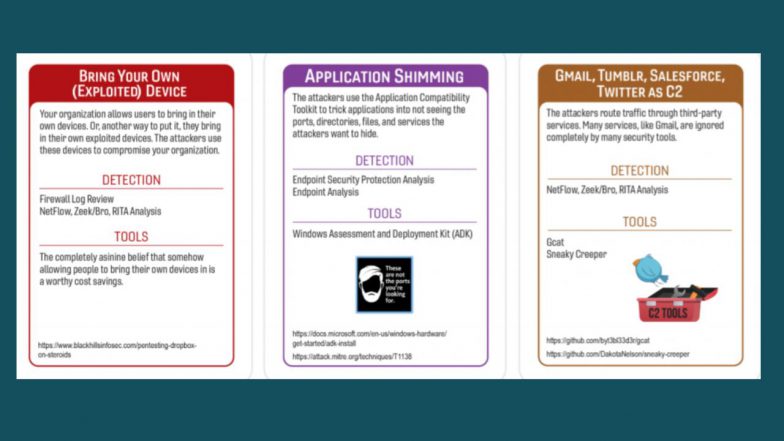
3:40 Red Card (Initial Compromise)
5:28 How the “Detections” were created
7:29 Yellow Card (Pivot and Escalate)
10:56 Brown Card (C2 and EXFIL)
11:35 Purple Card (Persistence)
12:32 Game Setup
13:12 Procedures and rolling your d20
14:34 Procedures being used
15:15 Green Cards (Consultants)
16:00 The Scenario
21:05 Actions that don’t require dice roll, “clarity vs. analysis”
27:30 First Procedure Dice roll and turn cool off counters
30:00 Debug Cautionary word from Jason
32:10 Procedure that works! (successful dice roll)
34:07 Revealing Attack Scenario cards upon successful roll
35:45 understanding the difference in established procedures and other procedures
39:56 Expansion Gray Card (Inject Card)
45:50 “at what point does an incident become a crisis?” Who on your team knows the difference?
52:57 Game Wrap up
53:40 Is this a plausible attack? Always ask that question at the end of the game
58:27 Goodbyes and Thank Yous
OnAir Post: Backdoors & Breaches
About
How the Game Works
- Roles: One player acts as the “Incident Master” (IM), creating a scenario based on a secret set of attack cards. The remaining players are the “Defenders,” working as the incident response team.
- Attack cards: The Incident Master secretly chooses one card from each of four categories to define the attack scenario:
- Initial Compromise: How the attackers first gained access.
- Pivot and Escalate: How the attackers moved through the network and escalated privileges.
- Persistence: How the attackers maintained their access over time.
- C2 and Exfil: How the attackers communicated with their systems and exfiltrated data.
- Procedure cards: The Defenders have a set of Procedure cards representing potential actions they can take to investigate the incident.
- Gameplay: On their turn, a Defender rolls a 20-sided die to determine if their chosen procedure is successful. A successful roll can lead to the Incident Master revealing one of the hidden attack cards, helping the Defenders uncover the full attack path.
- Goal: The game ends when the Defenders successfully reveal all the attack cards (a win) or when they fail to do so within a set number of rounds (a loss). After the game, teams discuss their successes and failures to improve their real-world incident response plans.
Source: Gemini AI Overview – 10/23/2025
Who should play?
The game is suitable for security professionals of all experience levels, from beginners to seasoned veterans. It is used by universities, government agencies, and Fortune 500 companies to help teams identify and fill gaps in their security programs and knowledge.
Source: Backdoors & Breaches is available as both a physical card deck and a free, open-source online version, making it accessible to both in-person and distributed teams. Source: Gemini AI Overview – 10/23/2025Open-source versions
Web Links