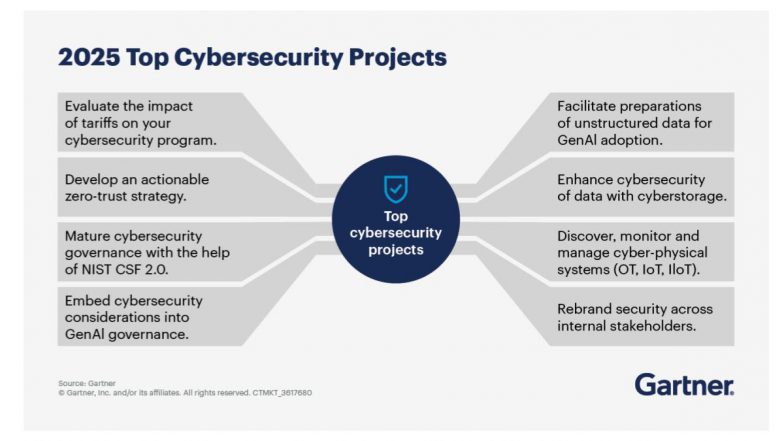
Summary
Prioritizing cybersecurity projects in 2025 should focus on addressing evolving threats from artificial intelligence (AI), securing expansive digital footprints from the cloud to the edge, and solidifying foundational security practices.
OnAir Post: Top Cyber Challenges for 2025
About
Implement AI-driven security tools
As AI-powered attacks become more sophisticated, defensive AI will be crucial for effective threat detection and response.
- AI-driven malware detection: Integrate AI and machine learning to analyze network traffic and endpoints for new malware variants that can morph and evade traditional, signature-based defenses.
- Deepfake detection: Combat sophisticated social engineering attacks with AI-driven tools that analyze videos and audio for inconsistencies that betray manipulated content.
- Security Operations Center (SOC) co-pilot: Deploy AI co-pilots within your SOC to automate mundane tasks and analyze massive data sets from firewalls and other logs. This allows human analysts to focus on complex, high-priority threats.
- AI incident response: Build an automated, AI-powered incident response system that can react instantly to predefined events like DDoS attacks or malware detection by performing tasks such as blocking IPs or isolating endpoints.
Strengthen security for expanding digital environments
Modern IT environments stretch across multiple clouds, remote devices, and the Internet of Things (IoT), each presenting a unique set of vulnerabilities.
- Refine your Zero Trust architecture: Implement continuous verification and robust access controls for every user and device, whether internal or external.
- Secure your supply chain: Vet third-party vendors and conduct regular risk assessments to mitigate supply chain attacks, which can compromise many downstream organizations through a single breach. A risk simulator can help model different scenarios.
- Improve cloud security posture: Implement Cloud Security Posture Management (CSPM) tools to automatically detect misconfigurations and vulnerabilities across your multi-cloud environment.
- Enhance IoT security: Develop stronger authentication measures, unique device credentials, and automated patching for the rapidly growing number of IoT devices on your network.
- Integrate IT and OT security: As industrial control systems (OT) converge with IT, implement specialized OT security software and micro-segmentation to protect against attackers disrupting production or infrastructure
Solidify foundational security practices
A layered defense is built on strong fundamentals. Prioritize these projects to raise your overall security baseline.
- Advanced authentication: Move beyond simple passwords by implementing phishing-resistant and passwordless solutions such as passkeys, biometrics, and multi-factor authentication (MFA) across your organization.
- Proactive incident response readiness: Create and regularly test detailed incident response playbooks for various threat scenarios, including ransomware and insider attacks. Conduct tabletop exercises to ensure all teams are prepared for a coordinated response.
- Establish human-centric security awareness: Invest in gamified or interactive training programs that simulate social engineering attacks like phishing, vishing, and pretexting to better educate employees on human-centric threats.
- Automate patch and vulnerability management: Integrate automated patching into your DevOps pipelines and orchestration frameworks to reduce the manual overhead of keeping all systems and devices updated.
- Continuous risk assessment: Regularly evaluate your attack surface through continuous vulnerability scans and penetration testing to keep pace with evolving threats.