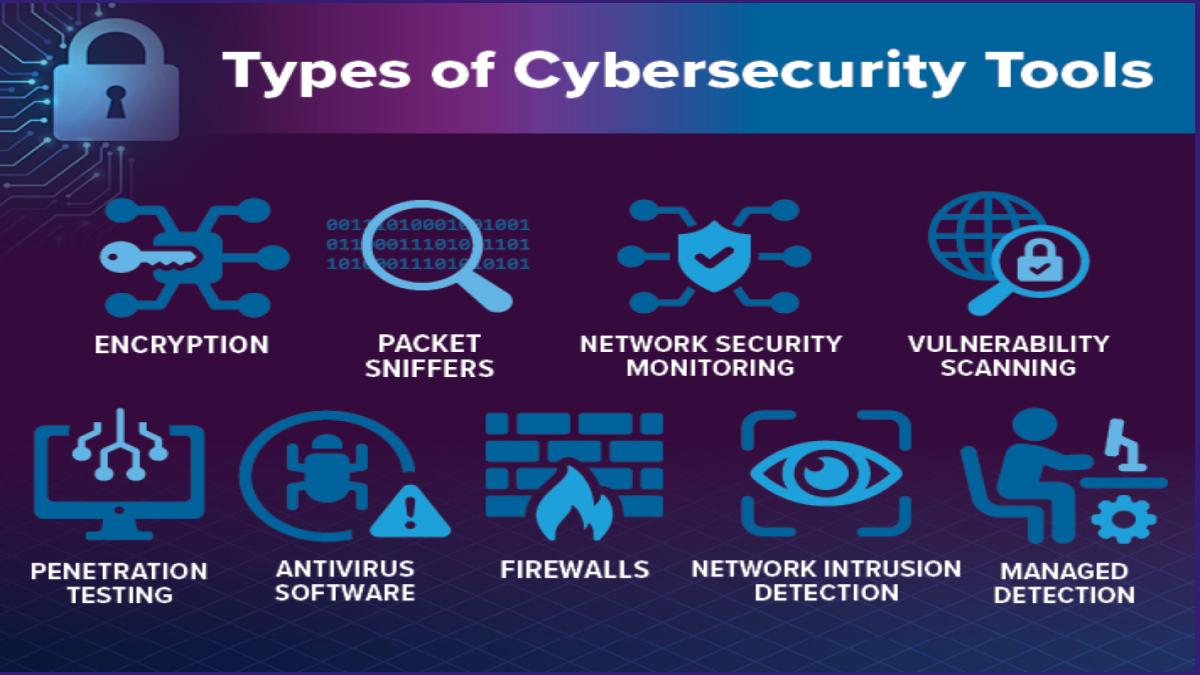
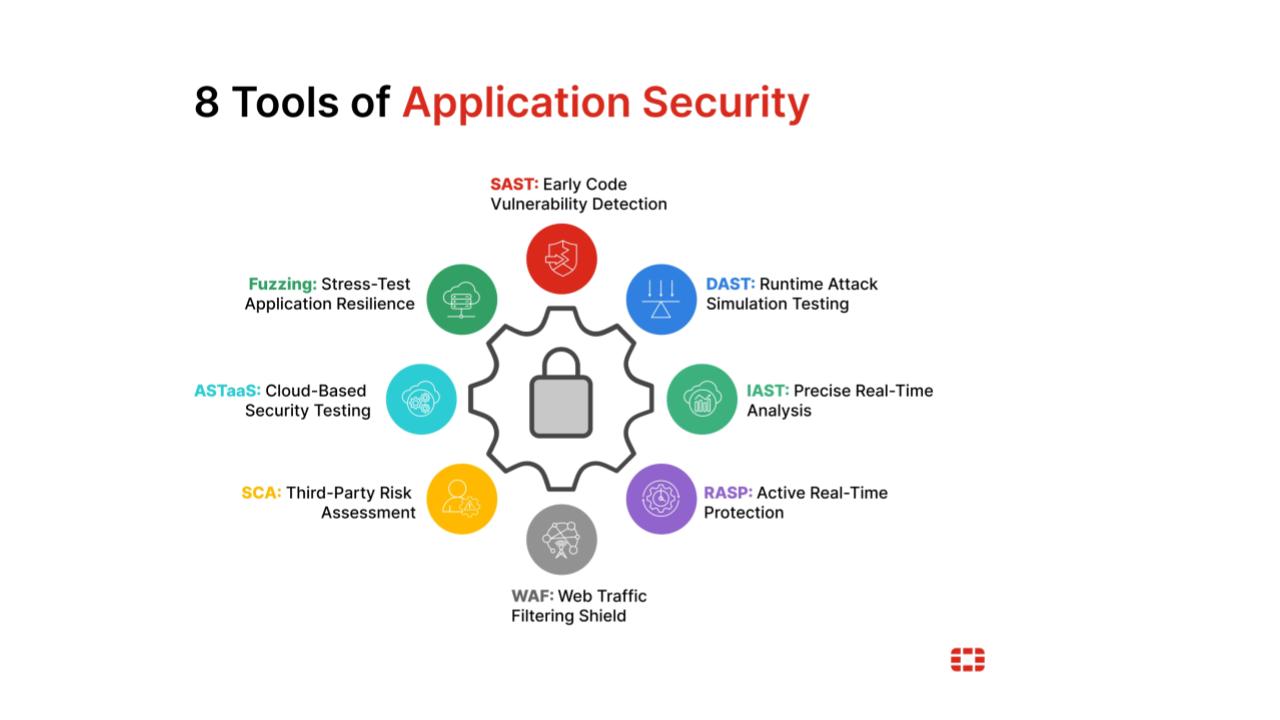
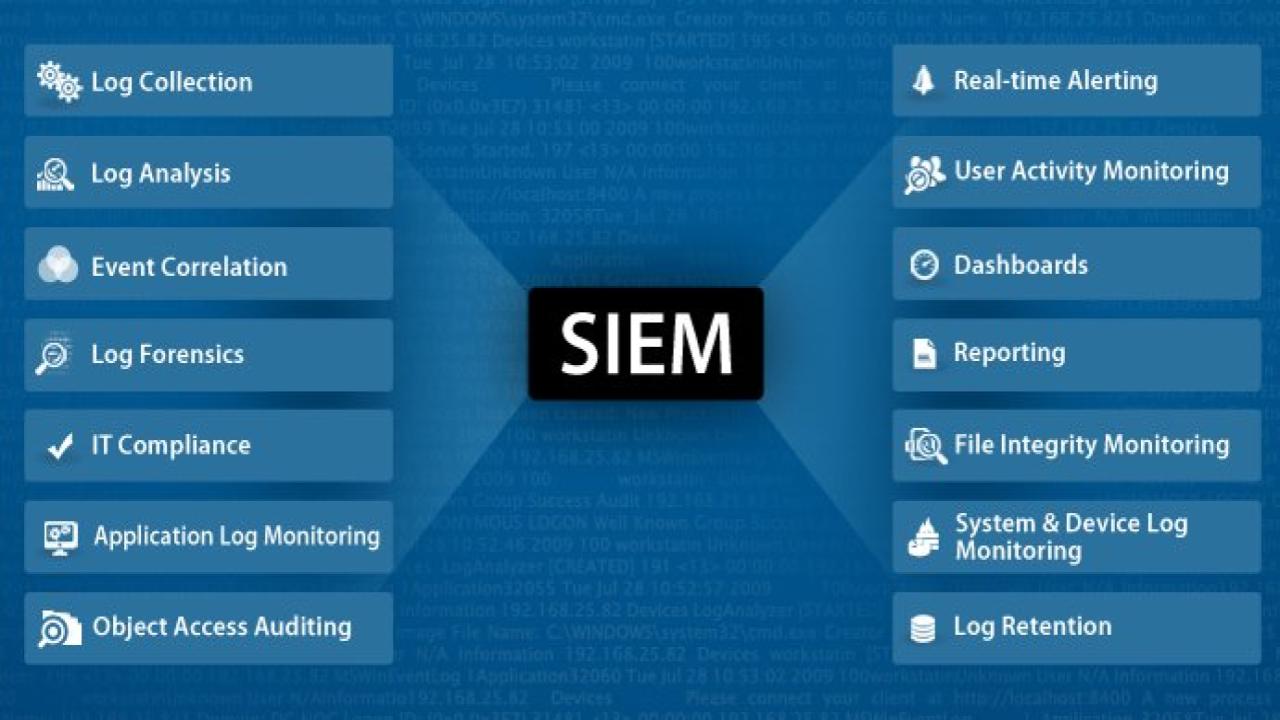
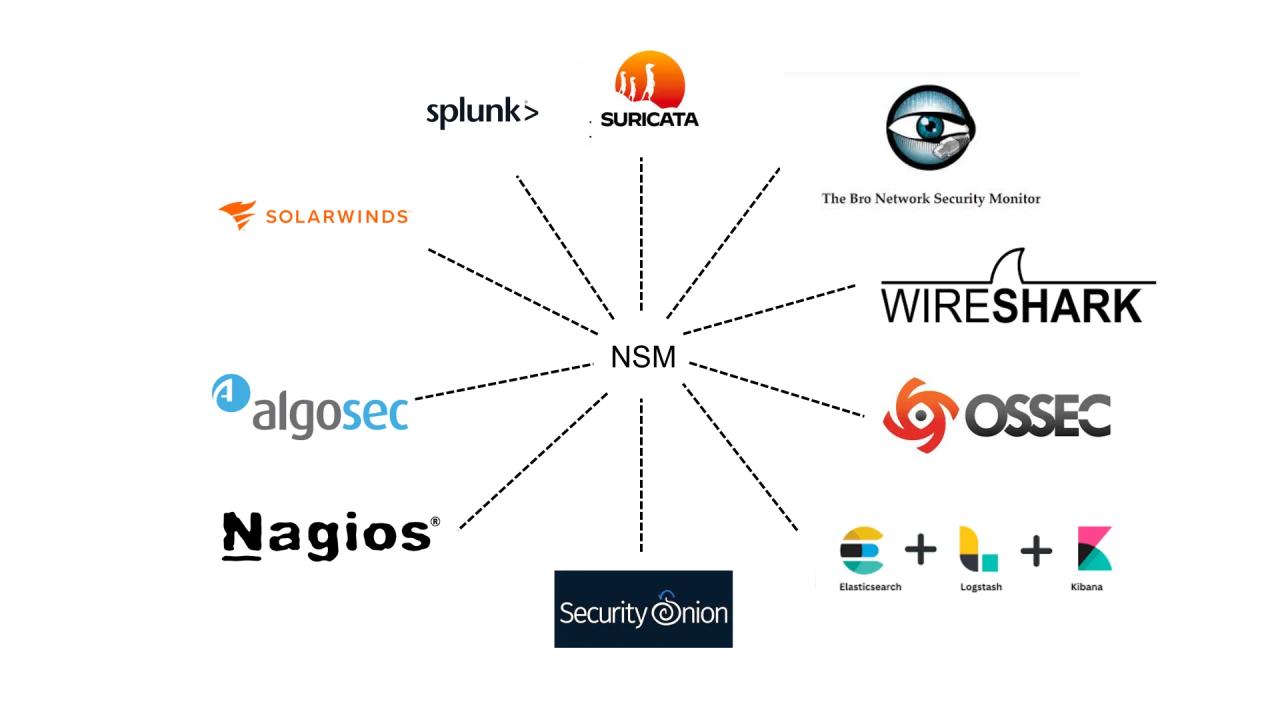
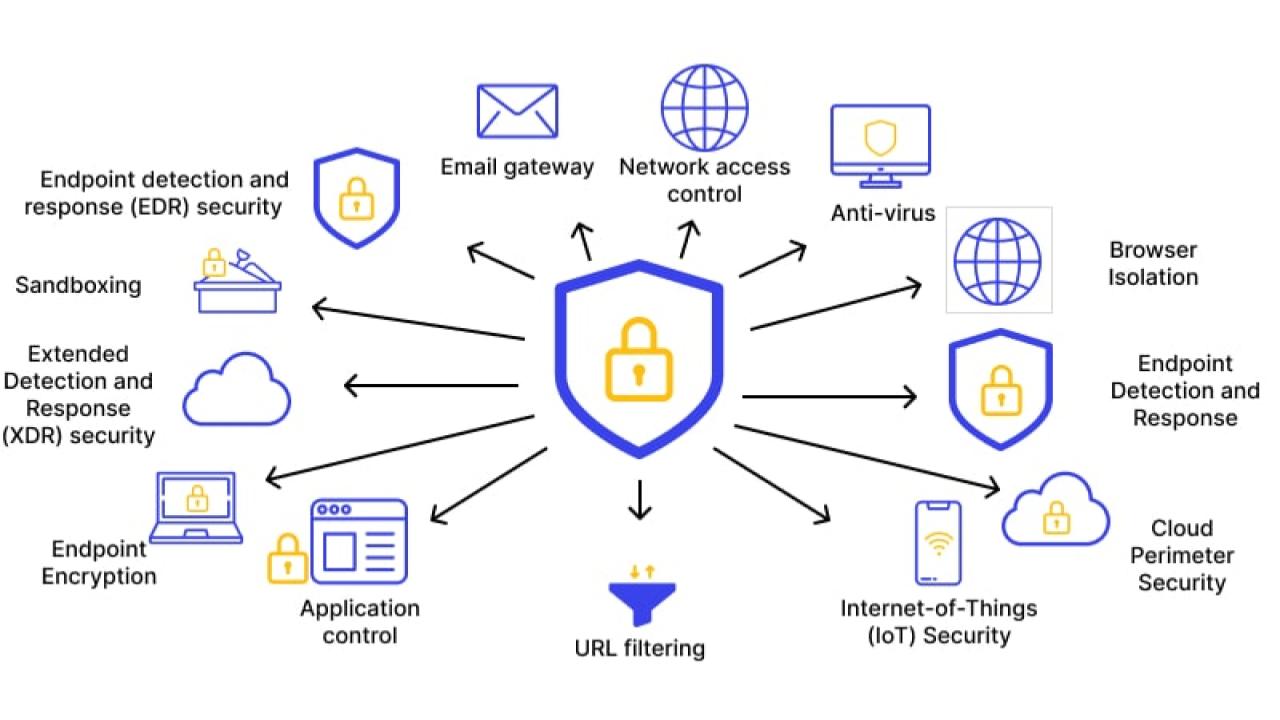
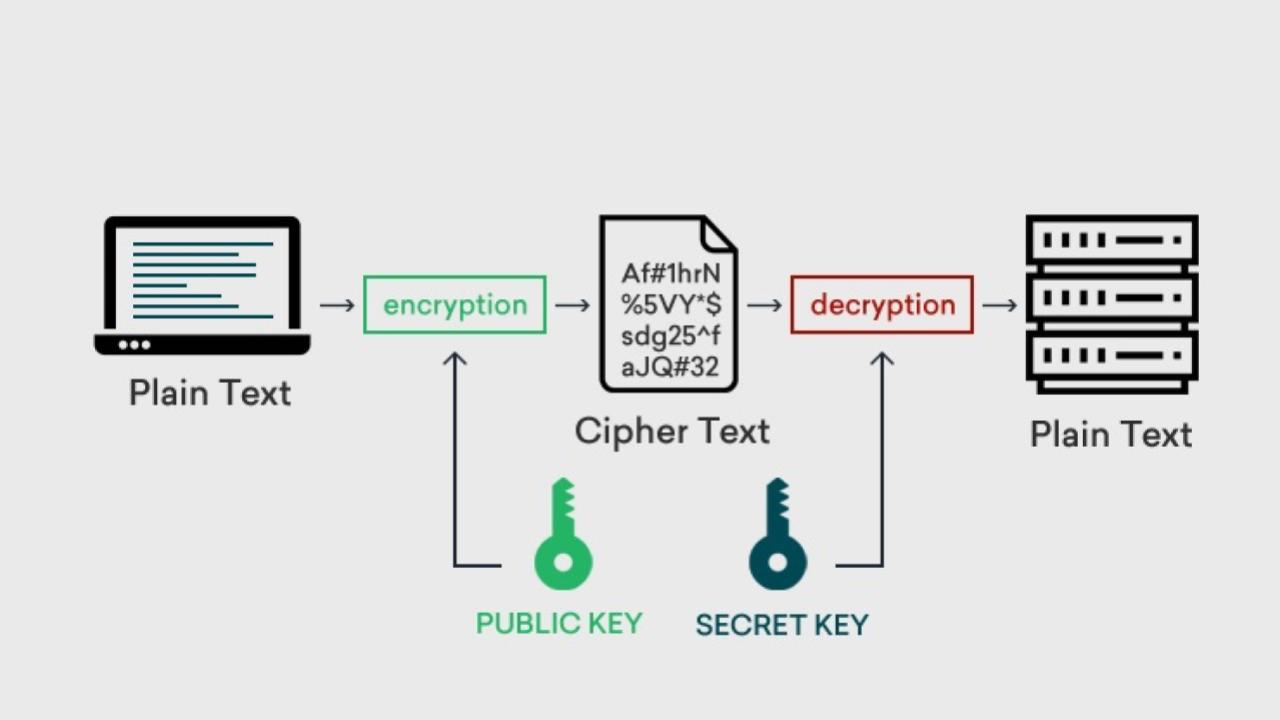
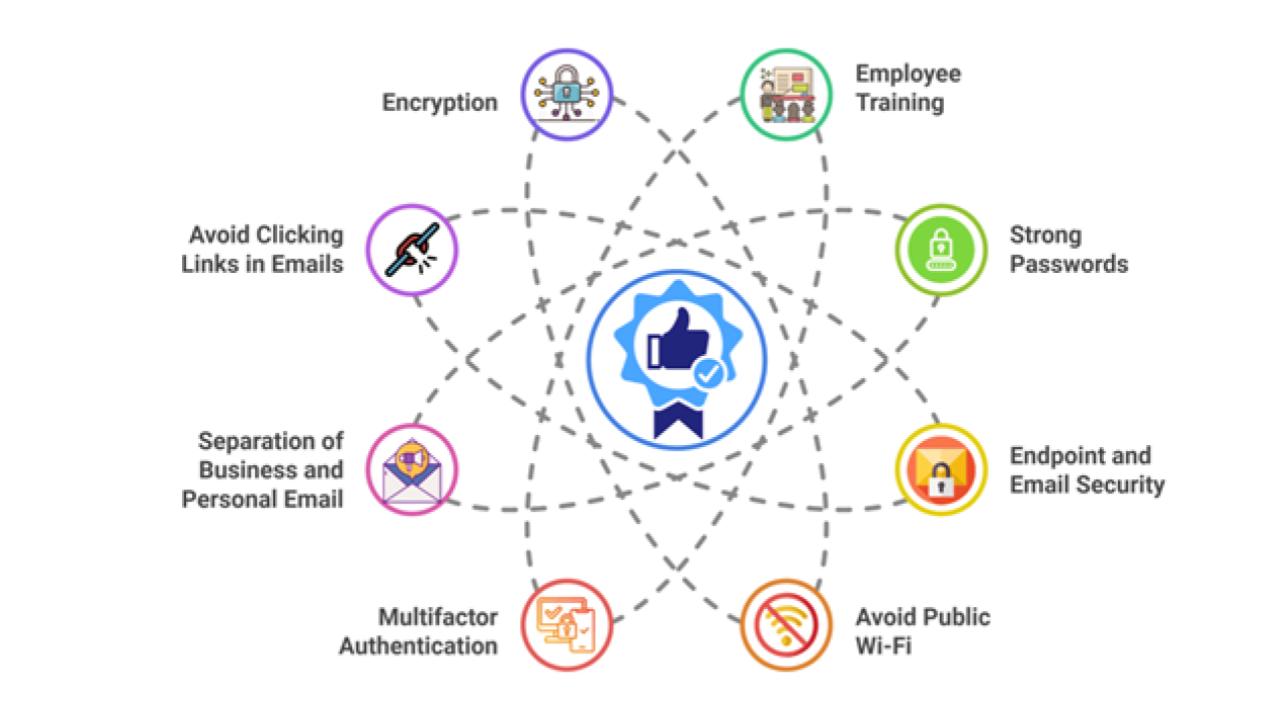
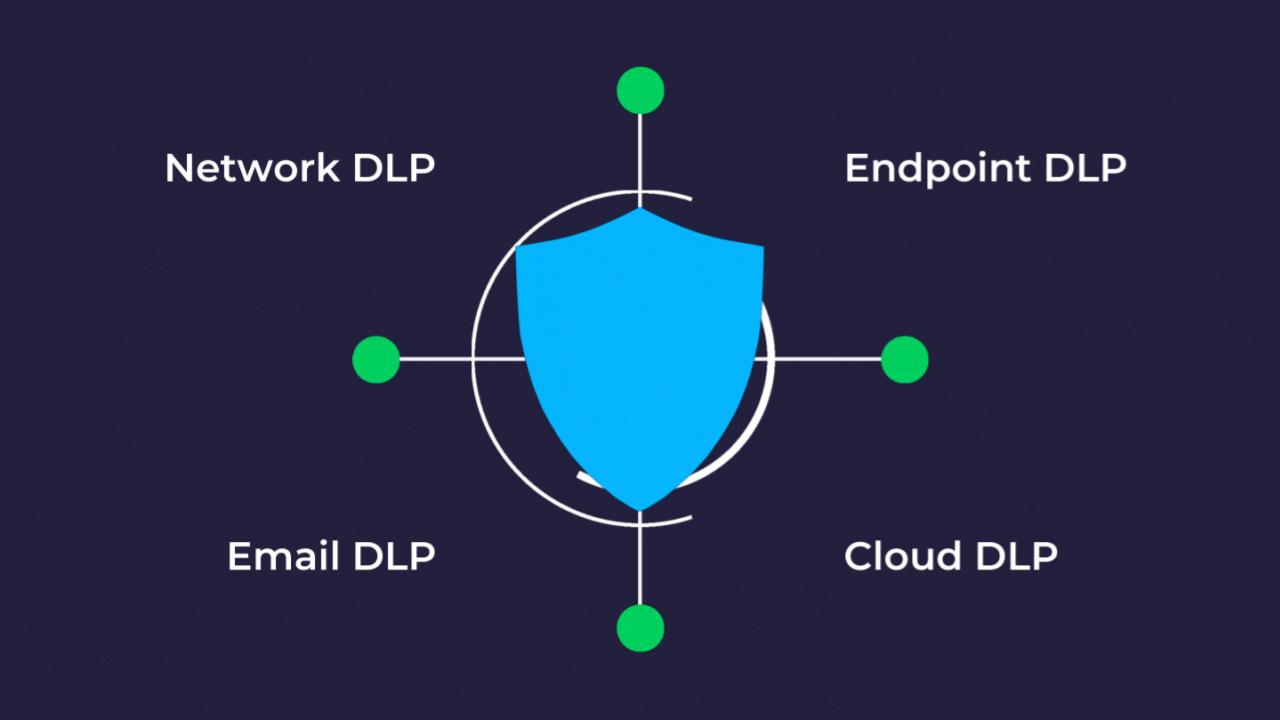
This is a list of cybersecurity information technologies. Cybersecurity concerns all technologies that store, manipulate, or move computer data, such as computers, data networks, and all devices connected to or included in said networks, such as routers and switches. All information technology devices and facilities need to be secured against intrusion, unauthorized use, and vandalism. Users of information technology are to be protected from theft of assets, extortion, identity theft, loss of privacy, damage to equipment, business process compromise, and general disruption. The public should be protected against acts of cyberterrorism, such as compromise or denial of service.
Cybersecurity is a major endeavor in the IT industry. There are a number of professional certifications given for cybersecurity training and expertise.[1] Billions of dollars are spent annually on cybersecurity, but no computer or network is immune from attacks or can be considered completely secure.
This article attempts to list important Wikipedia articles about cybersecurity.
Source: Wikipedia
OnAir Post: Cyber Tools