The Cyber Security onAir hub is an online community that brings together Experts, Organizations, Students, and anyone interested in Cybersecurity. To LEARN more about the field… DISCUSS relevant issues … and ENGAGE in positively addressing Cyber challenges.
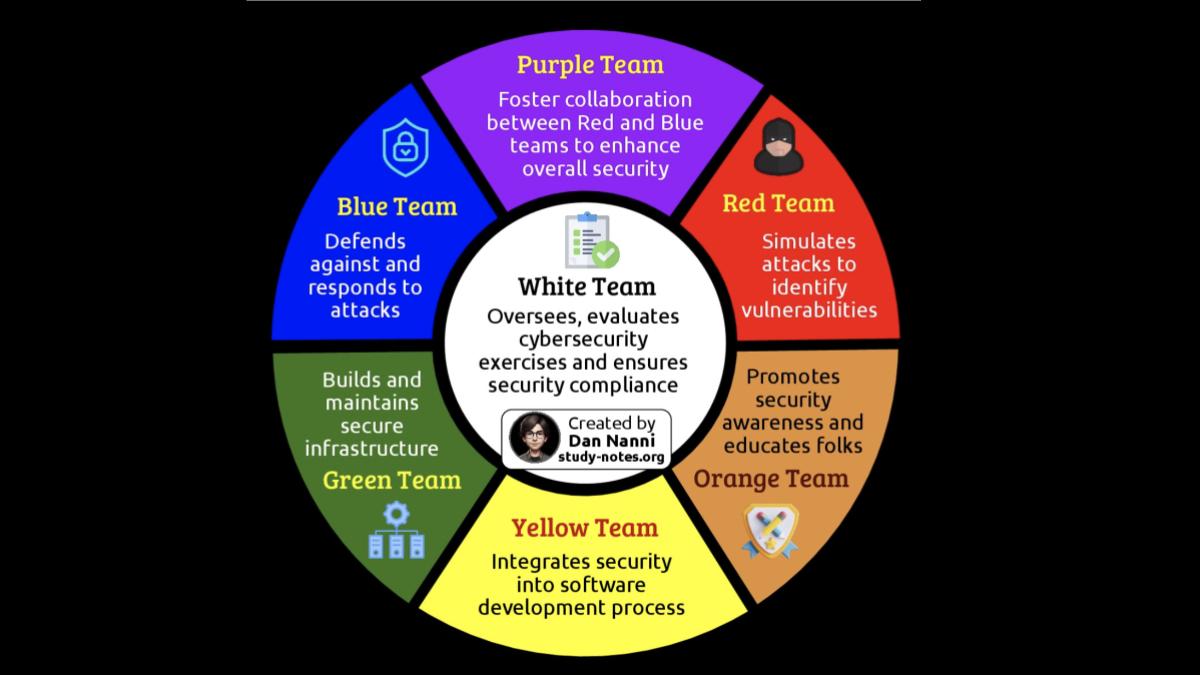
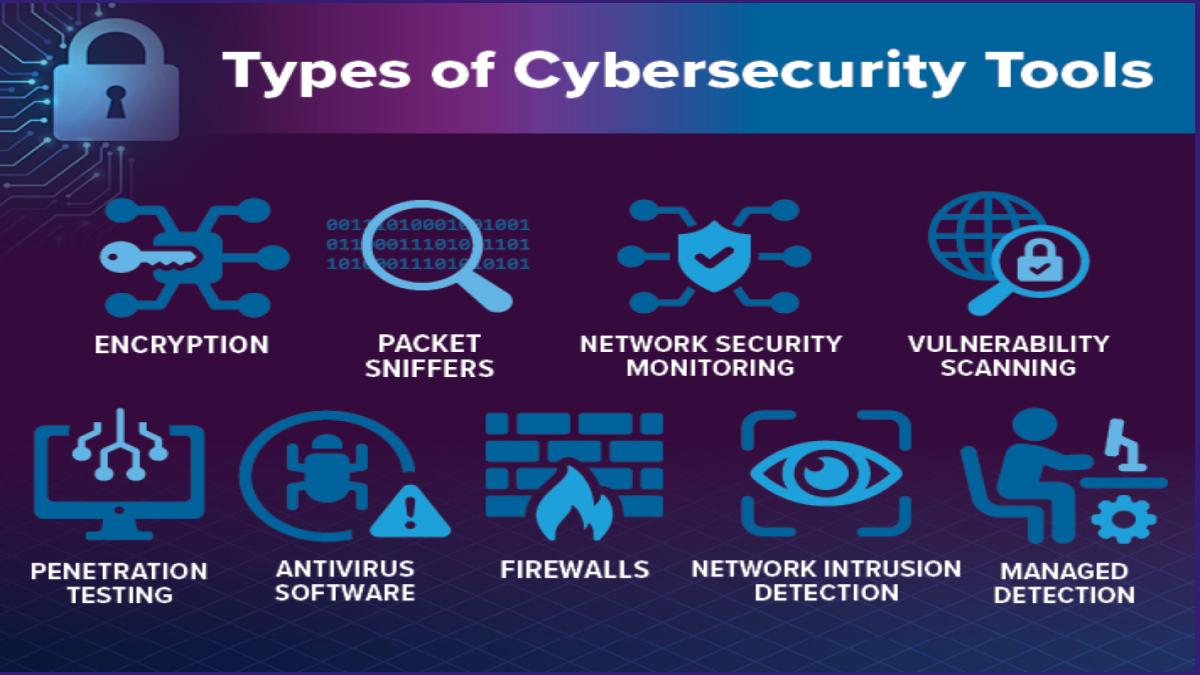
With our human-curated, AI-assisted onAir Knowledge Network platform, people can share and evolve cybersecurity knowledge about Cyber Challenges, Cyber Teams, Cyber Tools, and online cybersecurity Competitions … free from paywalls, algorithmic feeds, or intrusive ads.
Our Cyber hub facilitates relationships between novice and experienced cybersecurity engineers and the nonprofit and for profit organizations they represent. We provide profile posts for individuals and organizations which they control where and how their content is shared within a hub as well as shared with other networks like our AI Network Top Hub (see links under the onAir logo in the site header).
Our Cyber network of hubs facilitates relationships between novice and experienced Cyber stakeholders and the nonprofit and for profit organizations. We provide profile posts for individuals and organizations which they control where and how their content is shared within a hub as well as shared with other hubs in the AI & Science network like our AI Network Top Hub (see links under the onAir logo in the site header).
Cybersecurity onAir – 16/11/2025 (02:45)
https://www.youtube.com/watch?v=hwPbDiXcR9Q
OnAir Post: Cyber Security onAir Hub